Configuration for direct directory service access




Configuration for direct directory service access |




|
|
Here's how to set up and run the process of synchronizing users using direct communication mode:
1.To add a new domain configuration, go to SE Suite, the SE Configuration component
2.In the General
Domain ID: Enter the domain ID to connect to the LDAP server.
Connection String: Enter the connection string with the LDAP server. "ldap://<hostname>:<port>", remembering that the default value for the Microsoft Active Directory connection port is 389. For example: ldap://contoso.local:389 Connection type: Select which LDAP directory service to use: ▪Active Directory: Active Directory is a directory service implementation in the LDAP protocol that stores information about objects on a computer network and makes this information available to users and administrators of this network. It is a Microsoft software used in Windows environments, present in the Active directory. ▪OpenLDAP: OpenLDAP is an open source software that implements LDAP protocol. It is a directory service based on the X.500 standard. OpenLDAP is independent of the operating system. Several Linux distributions include the OpenLDAP package. The software also runs on the following operating systems: BSD, AIX, HP-UX, Mac OS X, Solaris, Microsoft Windows (2000, XP, 2003, 2008, Vista, Windows 7 and Windows 8) and z/OS. SSL Security: Check this option to use the SSL security protocol when accessing the system. The SSL protocol provides privacy and data integrity between two applications that communicate over the Internet. This is done through the authentication of the parties involved and the encryption of the data transmitted between the parties. Furthermore, this protocol helps prevent intermediaries between the two ends of the communications from gaining undue access or falsifying the data being transmitted. User: Enter the user's name to connect to the LDAP server. For example: "Synchronization User". The user name is used to connect to the directory service in the synchronization and simulation processes. Password: Enter the password for user authentication when connecting to the LDAP server.
3.In the General
Domain address: Enter the domain address to connect with the LDAP server. NTMLv2 port: This port is used for user authentication via NTLMv2. The connection test attempts an authentication using the credentials (login and password) provided below. If you do not intend to use this authentication mode, it may be ignored. Login for NTLMv2 connection test: Enter the user login to connect to the LDAP server. For example: "user.synch@contoso.local". This login will be used to test the connection to the directory service.
4.In the General
To view the directory/user structure contained in the directory service, it is recommended to use external tools such as "Active Directory Users and Computer" or "Apache Directory Studio". Refer to the Examples of LDAP filters for connection to a directory service section, for more examples of filters and directories.
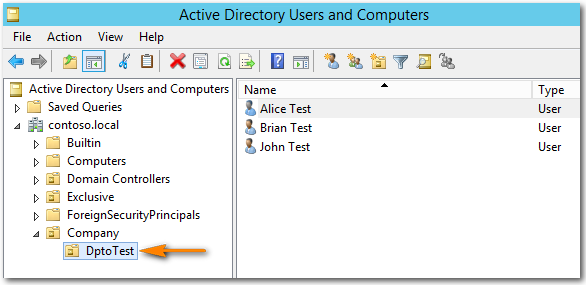 Active Directory Users and Computer presentation example
At this time, it is possible to validate the information by running a connection test; to do that, click on the
5.After that, save the settings you have made. Then, go to the General
To synchronize only user data, do not check the "Department and Position", "Access group" and "Team" options. However, it will not be possible to log into the system without this information.
The Attribute for first synchronization field is used to link an existing user to a domain. When a record with a value equal to that of the directory service is returned, the internal user is automatically linked to the domain, authenticating with the credentials maintained by the service. It is recommended to use the "User ID" field as an attribute for the first synchronization, since it is a field that has a unique value for each user, but other fields such as "Login", "E-mail" or "Name" may also be configured.
6.After that, fill in the fields in the Notification
7.Use the Synchronization
User: ▪ID # in domain controller: Enter the LDAP server attribute that should be used as the user ID #, that is, when importing the data, the attribute selected in this field will be saved in the database as the user ID #. ▪Name: Enter the LDAP server attribute to be used as the username, that is, when importing the data, the attribute selected in this field will be saved in the database as the username. ▪Login: Enter the LDAP server attribute to be used as the user login, that is, when importing the data, the attribute selected in this field will be saved in the database as the user login. ▪E-mail: Enter the LDAP server attribute to be used as the user e-mail, that is, when importing the data, the attribute selected in this field will be saved in the database as the user e-mail. ▪User ID: Enter the LDAP server attribute to be used as the user ID, that is, when importing the data, the attribute selected in this field will be saved in the database as the user ID.
Leader: ▪Synchronize leader: Check this option to enable system user leader to link the synchronization with the information configured in LDAP. By default, the system uses the "manager" field from the directory service to identify the leader and assemble the organizational hierarchy, comparing with the "distinguishedName" field of each record returned in the search (these two attributes can be customized). In order for the link to occur, both the user and its leader need to be listed in the search made using the given filter and directory. Therefore, you must adjust the search to meet this requirement or enable the "Ignore errors of leader not found" option if you wish to enable this function. ▪Leader ID # attribute (optional): Used to get the ID # of a leader user. By default, the system uses the "distinguishedName" attribute, or "entryDN" if the OpenLDAP connection type is being used. ▪Relationship attribute (optional): Indicates the ID # of the leader related to the users. By default, the system uses the "manager" attribute. ▪Do not synchronize user leaders with a circular reference: Consider three users: A, B and C. Users A and B are each other's leaders and B is C's leader. In this example, A and B would not be imported due to a circular reference, and C would also not be imported because their leader B could not be imported. By checking this option, the circular reference would be ignored, importing only A and B without a defined leader, but keeping B as the leader of user C, as C is not a part of the circular reference. ▪Ignore errors of leader not found: By using this option, if the leader synchronization option is enabled and the user leader is not contained in the user list for synchronization, there will be no errors and the user will be imported normally.
Initial parameters: ▪Initial parameters: The initial parameters will only be used when the user is created in SE Suite. These parameters will be used as defaults for all the users imported from the LDAP server. In other words, the Language, Enabled user, Locked user, Receive e-mailed news, Enable multiple logins and Max. number of connections options will only be used in the first access of new users, thus, they will not interfere with users already saved in SE Suite.
8.In the Synchronization
Department: ▪Department ID #: Enter the LDAP server attribute to be used as department ID #, that is, when importing the data, the attribute selected in this field will be saved in the database as department ID #. ▪Department name: Enter the LDAP server attribute to be used as department name, that is, when importing the data, the attribute selected in this field will be saved in the database as department name.
Initial parameters: ▪Inactive department: The initial parameters will only be used when the department is created in SE Suite. This parameter will be used as the default for all departments imported from the LDAP server. ▪Inactive position: The initial parameters will only be used when the position is created in SE Suite. This parameter will be used as the default for all positions imported from the LDAP server.
Position: ▪Position ID #: Enter the LDAP server attribute to be used as a position ID #, that is, when importing the data, the attribute selected in this field will be saved in the database as position ID #. ▪Position name: Enter the attribute of the LDAP server that is to be used as the position name, that is, when importing the data, the attribute selected in this field will be saved in the database as the position name.
New synchronized departments: ▪Default access groups: Default access group for new synchronized departments.
9.In the Synchronization
10. In the Synchronization
Team ▪Team ID #: Select the LDAP server attribute to be used as team ID #, that is, when importing the data, the attribute selected in this field will be saved in the database as team ID #. ▪Team name: Enter the LDAP server attribute to be used as team name, that is, when importing the data, the attribute selected in this field will be saved in the database as team name.
11. Save the settings you have made so far and close the screen.
12. On the Authentication (CM008) screen, click on the
13.
14. From this point onwards, it is possible to synchronize and track the process. Each synchronization generates a record in the synchronization history of users and teams (if enabled), allowing you to view the current status and record of the number of processed records. To track the current synchronization, click on the
15. In the User synchronization history section, the system provides the last 10 synchronization records for viewing.
Synchronization can have the following statuses: "Executing", "Executing with errors", "Loading AD information", "Loading SE Suite users", "Comparing the users of SE Suite with the users of AD", "Calculating permissions of users", "Finished" and "Finished with errors".
The "Calculating permissions of users" status indicates that new users are being added, and the system is creating the access permissions structure for them. This step may take a while depending on the number of new users. This step may take a while depending on the number of new users. The progress of user permissions processing can be tracked in the "With permission" column. Statuses that report errors refer to users with missing information, invalid formats, or conflicting information, and the reason for the error can be seen in the import details.
To view the import details (users with errors, updated, imported, and disabled), select the desired record and click on the
16. The Team synchronization history section is similar to the "User synchronization history" section, with differences in the details presented. This section will display teams with error, updated, imported and disabled teams.
17. By enabling synchronization scheduling, the process will run intermittently at midnight every day. Recurrence can be changed by going to the Monitoring
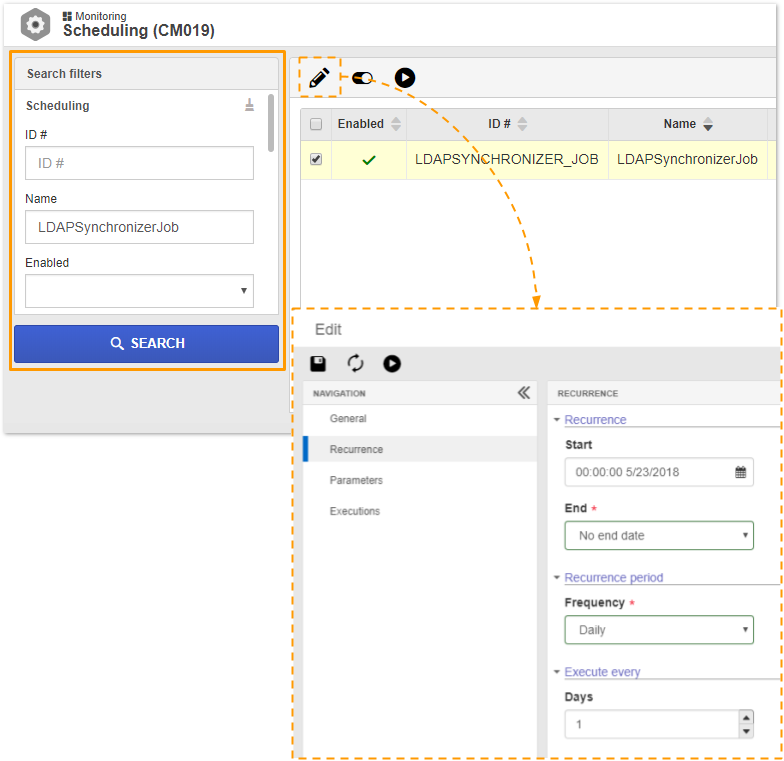 Scheduling recurrence change
18. There is a configuration in SE Suite that allows authenticating users not linked to a domain via SAML. This configuration is "Enable integrated authentication for users that are not synchronized" and can be found on the Configuration
This configuration was created for situations in which there is no user synchronization via LDAP or SCIM with SE Suite, but there is a need to authenticate the users manually created in SE Suite with a platform that uses SAML (Azure, Okta, and others).
In these cases, the "Enable integrated authentication for users that are not synchronized" configuration must be enabled and SAML must be configured in SE Suite through the Configuration
When the "Enable integrated authentication for users that are not synchronized" option is enabled:
▪The records of users that were not provisioned via LDAP or SCIM will be opened in SE Suite for manual editing, including the access password. ▪Single sign-on is possible for users via SAML (if SAML is configured in Configuration ▪Login via Single Sign-On will authenticate the user with the password created for them in the platform that uses SAML (Azure, Okta, etc.), and logging in with user and password (without single sign-on) will authenticate the user with their password and login created in SE Suite. ▪Single Sign-On on the SE Suite login screen has priority, that is, if the "User" and "Password" fields are filled out on the SE Suite login screen and the "Single Sign-On" button is clicked, the values entered in both fields are ignored. |